Zscalerのブログ
Zscalerの最新ブログ情報を受信
購読するTLS, SWG, and the New Encrypted World Order: Part 2
In Part 1 of this series, we delved into the meteoric rise of encrypted traffic, musing on how the widespread adoption of TLS brings both heightened security and a fair share of challenges.
We also explored how TLS inspection gives you an eagle's-eye view of network traffic, allowing you to deploy advanced security controls, such as URL filtering, intrusion prevention systems (IPS), access control, and more.
In Part 2, we will explore useful tactics and solutions that Zscaler delivers to help organizations deftly manage encrypted traffic, ensuring robust data protection without compromising accessibility.
Zero Trust Exchange: Where the Magic Happens
Let’s start by examining what happens when a user attempts to connect to a resource through the Zscaler Zero Trust Exchange (ZTE).
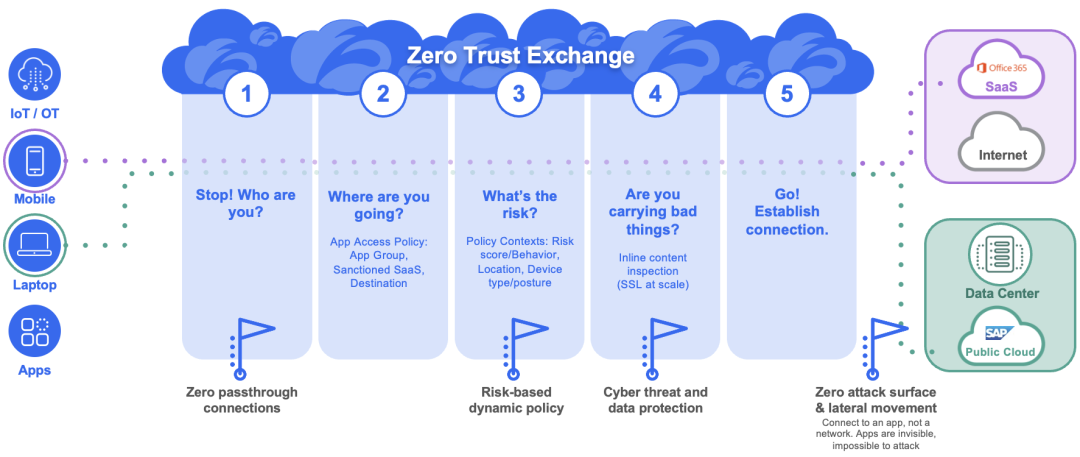
First, Zscaler intercepts the incoming traffic to identify the device, user, application or entity. It then determines the traffic's destination and access to applications based on the appropriate application policy—ensuring only authorized and necessary application access.
Zscaler considers multiple parameters to gain a comprehensive context of the incoming request, such as user risk score (Has this user engaged in risky behavior recently that might impact their trustworthiness in accessing critical applications?), device posture (Is the operating system up to date? Does it have security agents running?), device profile, and more, in addition to performing a full content risk analysis.
This helps create dynamic access control policies by leveraging the user risk score that assigns a dynamic risk score for individual users and keeps it updated periodically based on the users' latest behavioral trends—enabling ZTE to allow or restrict access based on device posture, user location, user risk score (based on their recent behavior), and multiple other factors.
Now, let's delve into our TLS inspection capabilities.
Peeking behind the TLS curtain with Zscaler
Beyond source, destination, and device characteristics, we take a deep look at the content. This is a critical step in the process, and is only possible with SSL/TLS inspection.
Zscaler’s content inspection is core to two sets of controls: Inline threat protection and outbound threat protection.
These protection capabilities comprise multiple layers of defense—starting with content categorization. This is where we employ AI/ML algorithms for URL filtering to categorize never-before-seen URLs. If the content of the page is allowed based on the URL filtering policy, we then run it through DNS and IPS analysis, and then through our malware analysis and Advanced Threat Protection engines.
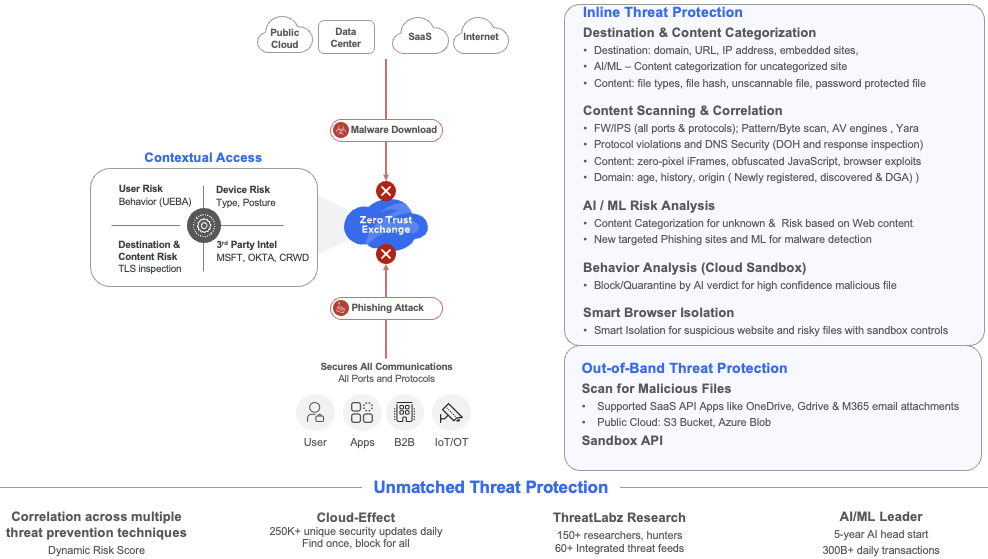
With our ‘single scan multi-action’ architecture, once we open a packet, we can perform a comprehensive set of activities including content inspection, content scanning, behavioral analysis, and cloud sandboxing all in one pass rather than doing it in a serial fashion.
This significantly reduces latency, ensuring optimal user experience without sacrificing layers of the security stack..
Furthermore, our threat intelligence is continuously enriched by insights gleaned from ongoing research from Zscaler ThreatLabz. Our dedicated research team, comprised of more than 150 researchers searching across 60+ threat fields and examining 300B+ daily transactions from the Zscaler cloud, feeds back data and insights so we can further reinforce our capabilities – to the tune of 250k signature updates per day.
TLS Inspection is critical to realize full value of modern SWG
Usually when we see minimal or no SSL decryption, we point out the wide spectrum of functionalities that can be unlocked by scanning this traffic—in addition to enhanced access control and data loss prevention capabilities.
Protecting encrypted data and sensitive information necessitates granular control mechanisms such as tenant-based restrictions and file type management. However, the implementation of these functionalities entails substantial investments in SSL inspection capabilities, which were not inherently designed to support man-in-the-middle proxies.
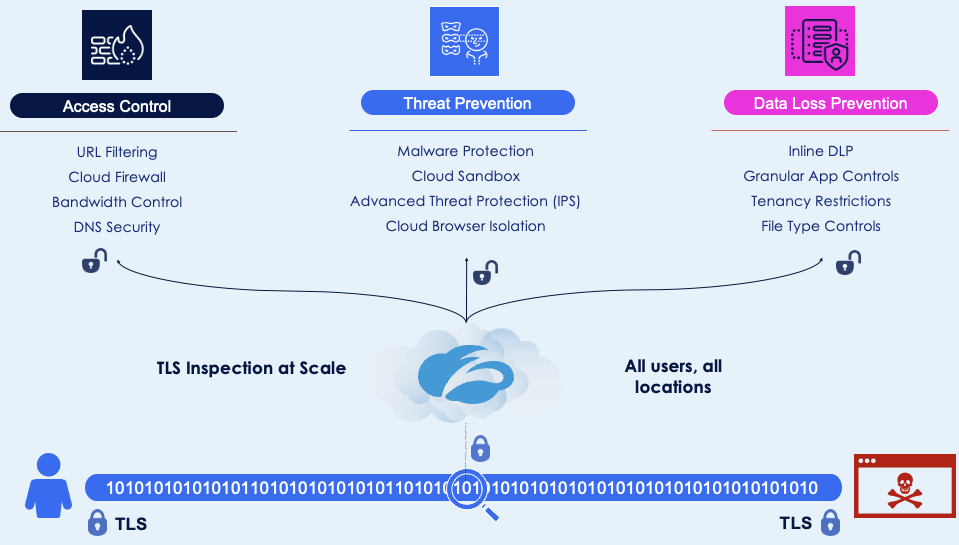
A strategic approach for TLS inspection at scale
Zscaler has innovatively devised strategies to ensure the integrity of data transmission, preventing sensitive information from going out and threats from coming in.
For achieving optimal outcomes for SSL inspection at scale, we adhere to five core principle in the form of pillars:
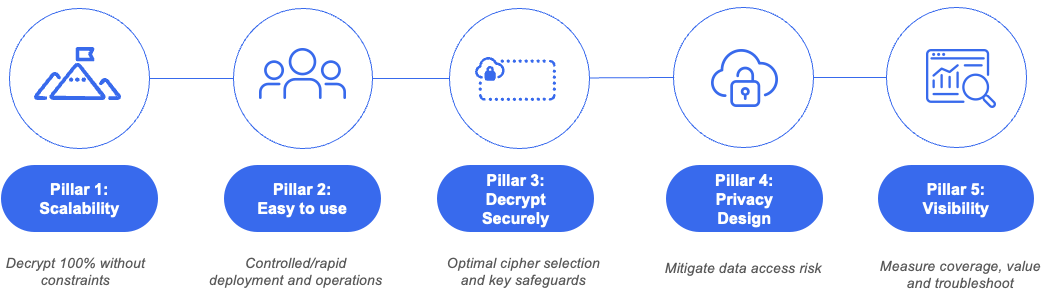
1. Scalability
SSL inspection is quite expensive and compute intensive in general. To achieve the required level of scalability, we ensure we have sufficient capacity, global coverage, and the right SSL acceleration in our entire global network to handle high volumes of encrypted traffic at line rate.
With over 150 locations worldwide and processing over 300 billion transactions daily, our architecture is designed for multitenancy, is distributed and purpose-built to handle high volumes of data and deliver a seamless end-user experience.
2. Ease of use
Simplifying SSL deployment is crucial, particularly during initial certificate enrollment, to avoid disrupting the user experience.
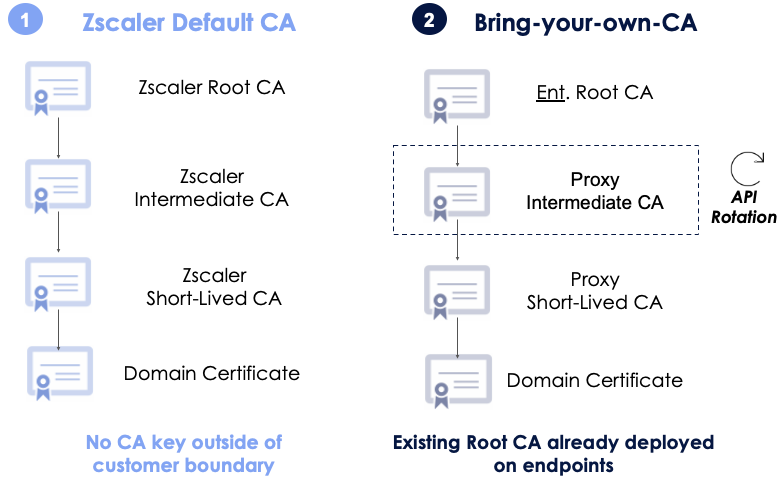
Zscaler offers two flexible deployment options. The first one is Zscaler Default CA for a straightforward setup, or a Bring Your Own CA (BYOCA) approach for customers with diverse PKI requirements.
In the Zscaler Default CA, we provide the root and intermediate certificates, which are used to sign the man-in-the-middle certificate. While this option is easy to use and comes out of the box, it does require the root certificate to be pushed out to all the endpoints to trust it.
With the BYOCA approach, we generate the private and public key pair stored within the Zscaler cloud boundary with measures in place to securely store and manage private and public key pairs. This facilitates certificate distribution through various deployment methods, including Zscaler Client Connector (ZCC) and third-party mobile device management (MDM) solutions.
3. Secure decryption
To enforce secure TLS usage, Zscaler provides granular control over encryption protocols, allowing users to specify minimum client and server-side versions. Furthermore, HTTPS 2 decryption is universally supported across all Zscaler cloud data centers.
Additionally, Zscaler offers a fully managed cloud hardware security module (HSM) service to safeguard encryption keys, ensuring robust security measures. Granular SSL policy enforcement, based on factors such as URL categories and geographic locations, enables phased SSL inspection deployment.
4. Privacy by design
Zscaler's architecture prioritizes security and privacy. We minimize and secure data throughout its life cycle—in use, in motion, and at rest. Our security controls are independently validated against top compliance frameworks, including DOD IL5. Additionally, Zscaler undergoes independent assessments to verify encryption controls, client key management, and the security of stored key information.
5. Measuring TLS inspection coverage
This is where we provide a lot of different techniques from QBR reports and cybersecurity risk reports where you can look at the traffic based on protocols. Users can essentially do a lot of troubleshooting by analyzing the logs based on different policy regions and the selected items there.
Once you measure the TLS inspection, there are different ways to quantify it. You can use different filters to see what is the value delivered across threat categories, different file types and across threat names.
By adhering to these core principles, Zscaler ensures that SSL inspection is conducted efficiently, transparently, and securely, maintaining the integrity of data transmission and enhancing network security posture.
Closing note: Security best practices for encrypted threats
In conclusion, using a zero trust architecture secures all connectivity holistically, while a cloud native proxy inspects and scans 100% of SSL/TLS traffic to prevent encrypted threats. Microsegmentation further reduces access, even for authenticated users. And, with zero trust, you can minimize the attack surface by making assets invisible to the internet, letting you eliminate vulnerable VPNs/firewalls.
Additionally, an AI-driven cloud sandbox isolates and quarantines unknown attacks, recognizing that all internet-facing services, including firewalls, are susceptible to discovery, attack, and exploitation.
To learn more, visit www.zscaler.com.




